Arm Your Business: Canon’s Guide to Mastering Information Security in the Future of Work - Business Insight
Arm Your Business: Canon’s Guide to Mastering Information Security in the Future of Work

Has your organisation experienced a cyber-attack in the past year? Let us guess. Your answer is probably “yes”.
According to a 2023 Cloudflare survey, 78% of cybersecurity managers in the Asia Pacific (APAC) reported at least one cybersecurity incident in the past 12 months. Among them, 80% encountered four or more incidents, and 50% experienced 10 or more, incurring losses ranging from $1 million to over $3 million1.
APAC is a global hotspot for cyber attacks
In 2021 and 2022, APAC alone accounted for 26%2 and 31%3 of global attacks respectively, making it the most targeted region in the world.
It also experienced the highest year-over-year increase in weekly cyber attacks, averaging 1,835 attacks per organisation in Q1 2023, compared to the global average of 1,2484. This prompted the World Economic Forum to label the region as the new ‘ground zero’ for cyber-crimes5.
Technology enables transformation — and cyber criminals
Home to some of the world’s most dynamic and fastest-growing digital economies, APAC is a natural hotbed for malicious actors. As more companies embrace new technologies for productivity and efficiency, they also widen their potential for information leaks.
What are some of the key vulnerabilities in the future workplace? Here are three examples:
1. Accelerated digital transformation
The pandemic had prompted many companies to quickly adopt new technologies to facilitate remote and hybrid work. Many did so at the expense of security, leaving vulnerabilities ripe for exploitation.
According to an IDC survey, this 'glaring oversight' resulted in 65% of APAC enterprises suffering ransomware attacks and breaches, with 83% experiencing business disruptions and downtime lasting from a few days to a few weeks6.
2. Hybrid work model
According to the 2024 Verizon Business Data Breach Investigations Report, 68% of data breaches involved ‘non-malicious human elements’ like social engineering attacks, errors, and misuse7.
Information security starts with your people. As more employees enjoy the convenience of remote work — conducting Teams meetings in public spaces, discussing business matters on WhatsApp, sharing unencrypted files on public Wi-Fi, using personal devices for work — companies without robust security measures and endpoint visibility will find it an uphill struggle to stop data theft and cyber-criminal activity.
3. The need for collaboration
To thrive in the future of work, companies must adopt new technologies like artificial intelligence (AI), cloud services, Internet of Things (IoT) devices, and smart mobile applications to automate workflows, enhance collaboration, and decentralise their IT infrastructure.
While this heralds a new era of connectivity, it also significantly expands the attack surface for cyber criminals, leaving vulnerable companies even more susceptible to cyber-attacks.
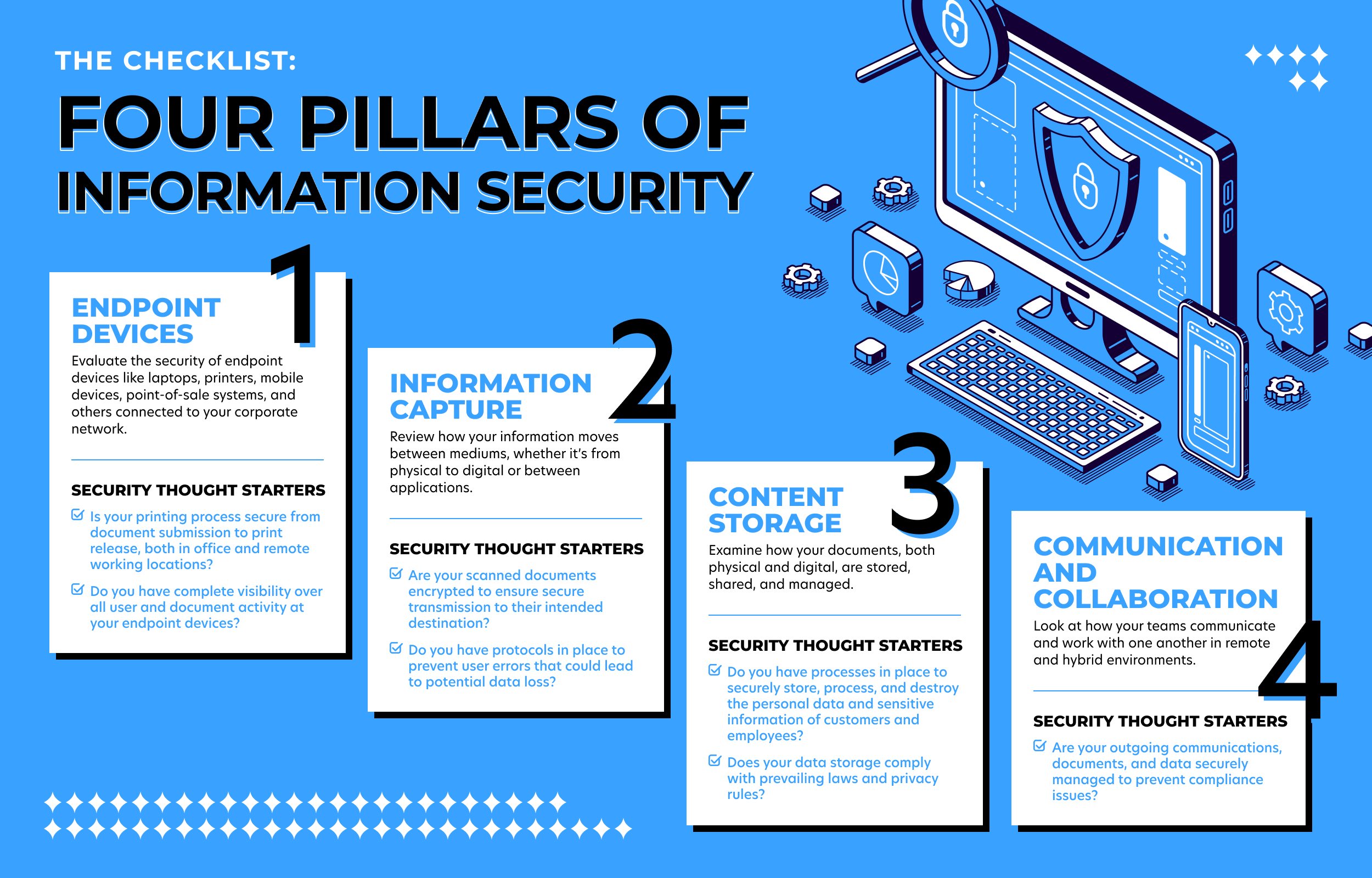
How secure is your business information? A checklist.
Information is at risk as soon as it’s created, whether on paper or digitally. To protect it, you need to secure it throughout its lifecycle —from creation and copying to storing, sharing, and ultimately destroying.
Test your business information security with our Four Pillars of Information Security!
Cutting-edge security solutions for the future of work
uniFLOW: Fortifies security in your print and scan environments
uniFLOW is a powerful integrated print, scan, and device management solution that simplifies and streamlines security challenges in your document management process.
How it protects:
- Secure network communication – all print jobs are encrypted and only released upon user authentication on destination device
- Secure scanning to all destinations including cloud services
- Multiple user authentication options
- Custom access control for different user groups
ThereforeTM: A secure way to store, share, and manage business information
ThereforeTM is a centralised information management platform that automates document workflows and streamlines the way you manage and share business information.
How it protects:
- Role-based access controls with multiple user authentication options
- Automatically backs up information for reliable disaster recovery
- Transparent and traceable logs and audit trails for system integrity and security
- Data encryption with anti-tamper controls
- Regular security audits for up-to-date and robust protection
Face Recognition Technology: An additional layer of access control
Authentication is key for Zero Trust environments. Face Recognition Technology adds an extra layer of security to existing options and easily integrates into print and scan setups with just a tablet or webcam.
How it protects:
- Anti-spoofing for enhanced security
- Deep learning capabilities identify distinctive facial features for seamless profile matching
- Prevents access sharing and identity theft
- Identifies individuals even when they’re wearing masks
Master Information Security in the Future of Work
As Larkin Ryder, Senior Director of Product Security at Slack points out, “There’s no doubt that bad actors have taken advantage of uncertainty and change over the last couple of years to exploit businesses and their employees. By following a few tips, though, we can slow them down, and raise the cost of attacks, while continuing to unlock the benefits of a hybrid future of work8.”
New technologies may create fresh opportunities for cyber exploitation, but that is no reason for us to stop embracing them. Cyber-crimes will persist. But a resilient cybersecurity defence will safeguard your information and arm your business in an ever-evolving future of work.
Get in touch to learn how we can help you mitigate risks with next-generation security solutions!
References:
- 2023, Cloudflare, Securing the Future: Asia Pacific Cybersecurity Readiness Survey, https://www.cloudflare.com/en-gb/lp/2023apjcsurvey/download/
- 2022, IBM, IBM X-Force Threat Intelligence Index 2022, https://newsroom.ibm.com/2022-02-23-IBM-Report-Manufacturing-Felt-Brunt-of-Cyberattacks-in-2021-as-Supply-Chain-Woes-Grew#:~:text=Additional%20findings%20from%20the%202022,60%25%20of%20attacks%20in%20Asia.
- 2023, IBM, IBM X-Force Threat Intelligence Index 2023, https://www.ibm.com/reports/threat-intelligence
- 2023, Check Point Research, Global Cyberattacks Continue to Rise with Africa and APAC Suffering Most, https://blog.checkpoint.com/research/global-cyberattacks-continue-to-rise/
- 2023, World Economic Forum, Why is the Asia Pacific region a target for cybercrime - and what can be done about it? https://www.weforum.org/agenda/2023/06/asia-pacific-region-the-new-ground-zero-cybercrime/
- 2022, IDC, Immunity is False: Why Every Business Needs to Take Cybersecurity Seriously, https://www.idc.com/ap/event/security-masterminds-2023/blog-immunity-is-false
- 2024, Verizon Business, 2024 Data Breach Investigations Report (2024 DBIR), https://www.verizon.com/business/resources/reports/dbir/?CMP=OOH_SMB_OTH_22222_MC_20200501_NA_NM20200079_00001
- 2022, Tech Wire Asia, Five tips to ensure a secure hybrid and remote working experience, https://techwireasia.com/11/2022/five-tips-for-to-ensure-a-secure-hybrid-and-remote-working-experience/
